SSTI (Server Side Template Injection)
loading...
. . . . . .

Server side Template Injection or SSTI occurs when an attacker provides a malicious input to the application template which leads to executing commands on the server side. This vulnerability usually occurs when the application fails to validate the user input and embeds it into the template engine which leads to RCE.
A template engine enables you to use static template files in your application. At runtime, the template engine replaces variables in a template file with actual values and transforms the template into an HTML file sent to the client. This approach makes it easier to design an HTML page. You can visit here to find out more about template engines.
Some of the most popular template engines can be listed below:
SSTI can occur when the application is failing to validate the input from the user and inject the code into one of the template engines (whichever is implemented on the server) and lead to RCE.
Now, as in any vulnerability, before we can exploit it, it is necessary to detect it. Finding SSTI may get tricky as there are multiple template engines available and each of them has a different payload/technique to exploit it.
Hence, as an initial step, we can start by using the polyglot payload as : ${{<%[%'”}}%\
Also, the vulnerability can be identified by using the following plain text context :
To check if the server is vulnerable to SSTI, you should be able to spot the difference between the responses with regular data and one with the injected payload. In case the application is vulnerable it can raise an exception or an error message which can be used to identify the template and its version.
Also, if the injected payload is processed by the server and the response contains the processed data, it can be then useful in determining the template engine.
The below diagram can also be referred to identify the template engine in use.
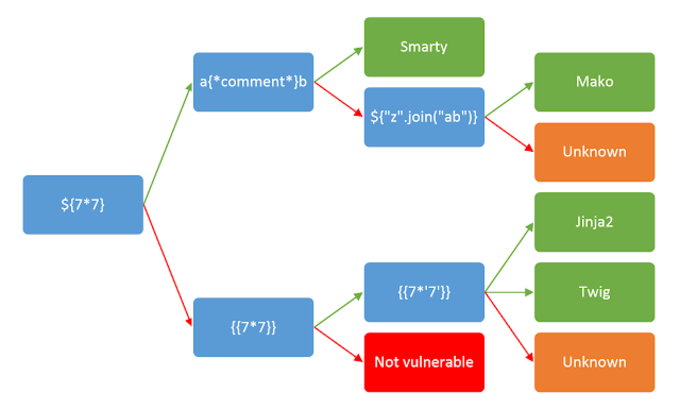
To identify if the application is vulnerable, the following to-do list can be referred to:
SSTI generally has a severe impact on the server as it can lead to remote code execution and take full control over the back-end server. Even if an attacker fails to achieve the code execution, sensitive files/data can also be retrieved via this vulnerability. There might also be some rare cases where SSTI is not critical.
To reduce the burden of manual testing, Tplmap can be used to detect the vulnerability, identify the template, and exploit it. It is a widely used tool for SSTI.
<r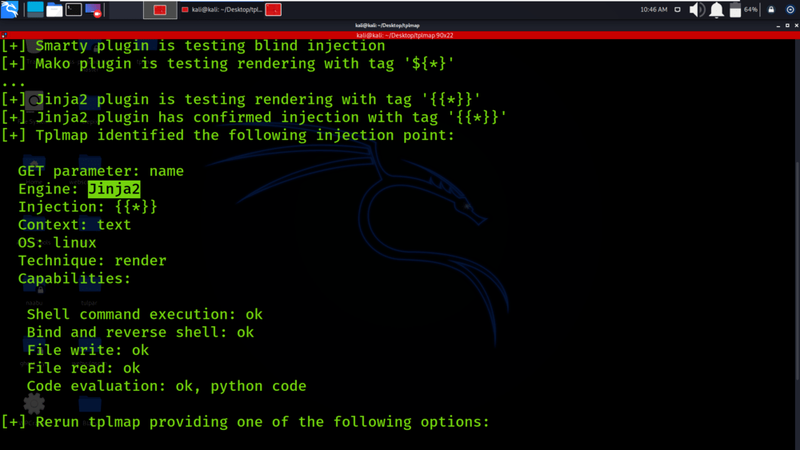
Also, more on Tplmap can be found here.
Although you may find different cheatsheets online for the cause, the below links can help in better serving the cause:
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection
Remediations for the SSTI may differ as there are different template engines in use.
Although there are 2 common suggestions to remediate this vulnerability:
https://www.cobalt.io/blog/a-pentesters-guide-to-server-side-template-injection-ssti
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection
https://expressjs.com/en/guide/using-template-engines.html
https://github.com/epinna/tplmap
Mr.Rushikesh Dave is the Information Security Consultant at qSEAp Infotech pvt. ltd.